
Embracing Multi-Factor Authentification
Written by Cisilion CTO, Rob Quickenden
Cyberattacks aren’t slowing down, and it’s worth noting that many attacks have been successful without the use of advanced technology. For even the largest most security averse company, all it takes is one compromised credential or one legacy application to cause a data breach.
This underscores how critical it is to ensure password security and strong authentication across your organisation and whilst there are many many solutions out there that can protect networks, applications and data, there is one simple thing that organisations can do, regardless of size and sector that can have a significant impact on protecting cyber–attacks and breach through compromised credentials.

Where Are You Most Vulnerable?
A recent report from the SANS Software Security Institute, the most common vulnerabilities include:
Corporate Email Compromise
Where an attacker, often called bad-actor, gains access to a corporate email account, such as through a phishing or spoofing attack (emails that look like they are from IT or a trusted source that gets users to “handover” their logon credentials), and uses it to exploit the system, and steal data or compromise your business. Accounts that are protected with only a User ID and password are easy targets.
Legacy Protocols
Old email clients and many “stock smartphone email clients” can create a major vulnerability since applications that use these old basic protocols, such as SMTP, were not designed to leverage or use modern security technologies such as Multi-Factor Authentication (MFA). So even if you require MFA for most use cases, if legacy protocols are enabled, attackers will search for opportunities to use outdated browsers or email applications to force the use of less secure protocols.
Reusing Passwords
This is where attacks such as “password spray” and “credential stuffing attacks” come into play. Common passwords and credentials compromised by attackers in public breaches are used against corporate accounts to try to gain access. It’s considered that more than 70% of passwords are duplicates and used on other public sites such as shopping or consumer sites, this has been a successful strategy for many attackers for years and it’s easy to do. Most users re-use passwords because many believe that complex passwords (a mix of letters, numbers and symbols) make passwords and accounts secure – but it can actually have a counter effect since passwords are more likely to be re-used.

What you can do to protect your company?
There are multiple simple steps that can and should be undertaken to provide some basic account and security hygiene.
Administrators can quickly help prevent many of these attacks by banning the use of bad passwords (Azure AD can do this naively), blocking legacy authentication, and through basic awareness and training to staff on how to spot common phishing attacks.
Whilst all this will help, by far the most effective step you can take as a business is to turn on and require Multi-Factor Authentication (MFA). This extra layer of user account protection creates a very effective barrier and layer of security that makes it incredibly difficult for attackers to log on or use stolen/compromised credentials even if a user “hands them over” as a result of a successful phishing attack.
“Simply put, MFA can block over 99.9% of compromising attacks”
With MFA, knowing or cracking the password isn’t enough to gain access since the user will be challenged to enter a code, respond to a text sent to their phone or approve logon via an app on a device that they have in their possession. To learn more, read Your Pa$$word doesn’t matter.
MFA is easy to enable and use
According to the SANS Software Security Institute, there are two primary obstacles to adopting MFA implementations today:
- A misconception that MFA requires external hardware devices.
- Concern about potential user disruption or concern over what may break.
When we have these conversations with customers, the 2nd point is usually the most common – “the owner won’t like it” or “what if stops person x from logging on and they cant talk to IT?”
No banking app allows their customers to access their services these days without some form of MFA and we all, as we have to, simply accept this so why should accessing your company’s data be any different?
Depending on your organisations choice of MFA technology and the level of licensing they have in place, services such as MFA can be used in conjunction with Risk-Based Conditional Access – which is a feature included within Azure Active Directory.
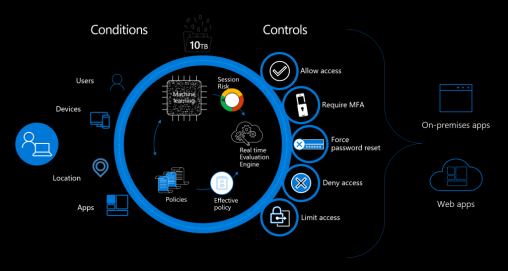
Risk–Based Conditional Access is essentially adaptive authentication which looks at a number of different risk factors to determine what and how to allow a user to gain access to resources. In the MFA example, RBCA can be configured to now need MFA to be used when on a corporate device when in the office but enforced whenever users are remote or on a non-corporate or non-encrypted device.
Your Next Steps – Proofpoint MFA Research
Want to learn more about Multi-Factor Authentification? Read more from our CTO Rob Quickenden as he evaluated SC Magazine report from Proofpoint researchers who studied hundreds of thousands of unauthorised logins. Click here to read the summary.
Read: SHOULD YOU PRIORITISE MULTI-FACTOR AUTHENTICATION?
Aspects of this article include content from Melanie Maynes, Microsoft Security
